Size of this PNG preview of this SVG file: 525 × 513 pixels. Other resolutions: 246 × 240 pixels | 491 × 480 pixels | 786 × 768 pixels | 1,048 × 1,024 pixels | 2,096 × 2,048 pixels.
Original file (SVG file, nominally 525 × 513 pixels, file size: 25 KB)
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 18:00, 19 October 2024 |  | 525 × 513 (25 KB) | GKNishimoto | File uploaded using svgtranslate tool (https://svgtranslate.toolforge.org/). Added translation for pt-br. |
| 11:29, 2 August 2018 |  | 525 × 513 (20 KB) | FlippyFlink | Aligned name Bob and Alice with (portable) Inkscape editor. | |
| 08:36, 7 July 2017 |  | 525 × 513 (20 KB) | Winstonlee | Reverted to version as of 21:11, 21 August 2006 (UTC) | |
| 06:04, 6 July 2017 |  | 525 × 513 (20 KB) | Winstonlee | Typically Alice wants to send message to Bob using Bob's public key, instead of the reverse. | |
| 21:11, 21 August 2006 |  | 525 × 513 (20 KB) | Davidgothberg | Improved image. | |
| 19:02, 21 August 2006 |  | 544 × 513 (20 KB) | Davidgothberg | Improved image. | |
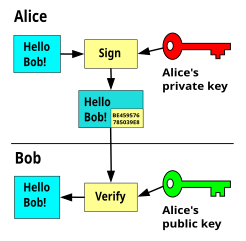
| 07:42, 7 August 2006 |  | 530 × 400 (15 KB) | Davidgothberg | Public-key cryptography / asymmetric cryptography, encryption. A message that is encrypted with the public key can only be decrypted with the secret key. The public key can NOT decrypt the message. This means any one can send encrypted messages to the ow |
File usage
The following 6 pages use this file:
Global file usage
The following other wikis use this file:
- Usage on ar.wikipedia.org
- Usage on bn.wikipedia.org
- Usage on ca.wikipedia.org
- Usage on de.wikipedia.org
- Usage on en.wikibooks.org
- Cryptography/A Basic Public Key Example
- A-level Computing 2009/AQA/Problem Solving, Programming, Operating Systems, Databases and Networking/Communication and Networking/Internet Security
- User:Zacchaeusluke/sandbox
- A-level Computing/AQA/Problem Solving, Programming, Operating Systems, Databases and Networking/Communication and Networking/Internet Security
- A-level Computing/AQA/Paper 2/Fundamentals of communication and networking/Internet security
- Cryptography/Print version
- Usage on fr.wikibooks.org
- Usage on hy.wikipedia.org
- Usage on id.wikipedia.org
- Usage on it.wikipedia.org
- Usage on ja.wikipedia.org
- Usage on ka.wikipedia.org
- Usage on ko.wikipedia.org
- Usage on mg.wikipedia.org
- Usage on ml.wikipedia.org
- Usage on or.wikipedia.org
- Usage on pt.wikipedia.org
- Usage on ru.wikinews.org
- Usage on simple.wikipedia.org
- Usage on th.wikipedia.org
- Usage on tl.wikipedia.org
- Usage on www.wikidata.org
- Usage on zh-yue.wikipedia.org