Privacy-Preserving Distributed Analytics in Fog-Enabled IoT Systems
- PMID: 33138072
- PMCID: PMC7662678
- DOI: 10.3390/s20216153
Privacy-Preserving Distributed Analytics in Fog-Enabled IoT Systems
Abstract
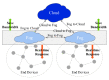
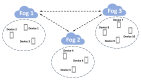
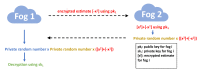
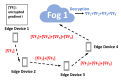
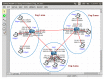
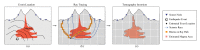
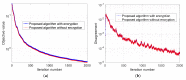
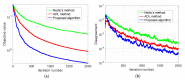
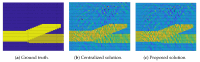
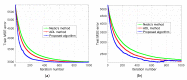
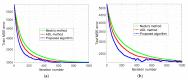
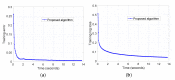
The Internet of Things (IoT) has evolved significantly with advances in gathering data that can be extracted to provide knowledge and facilitate decision-making processes. Currently, IoT data analytics encountered challenges such as growing data volumes collected by IoT devices and fast response requirements for time-sensitive applications in which traditional Cloud-based solution is unable to meet due to bandwidth and high latency limitations. In this paper, we develop a distributed analytics framework for fog-enabled IoT systems aiming to avoid raw data movement and reduce latency. The distributed framework leverages the computational capacities of all the participants such as edge devices and fog nodes and allows them to obtain the global optimal solution locally. To further enhance the privacy of data holders in the system, a privacy-preserving protocol is proposed using cryptographic schemes. Security analysis was conducted and it verified that exact private information about any edge device's raw data would not be inferred by an honest-but-curious neighbor in the proposed secure protocol. In addition, the accuracy of solution is unaffected in the secure protocol comparing to the proposed distributed algorithm without encryption. We further conducted experiments on three case studies: seismic imaging, diabetes progression prediction, and Enron email classification. On seismic imaging problem, the proposed algorithm can be up to one order of magnitude faster than the benchmarks in reaching the optimal solution. The evaluation results validate the effectiveness of the proposed methodology and demonstrate its potential to be a promising solution for data analytics in fog-enabled IoT systems.
Keywords: distributed analytics; fog computing; internet of things; privacy-preserving.
Conflict of interest statement
The author declares no conflict of interest.
Figures
Similar articles
-
An Overview of Fog Data Analytics for IoT Applications.Sensors (Basel). 2022 Dec 24;23(1):199. doi: 10.3390/s23010199. Sensors (Basel). 2022. PMID: 36616797 Free PMC article. Review.
-
Privacy-Preserving Data Aggregation against False Data Injection Attacks in Fog Computing.Sensors (Basel). 2018 Aug 13;18(8):2659. doi: 10.3390/s18082659. Sensors (Basel). 2018. PMID: 30104516 Free PMC article.
-
Hybrid computing framework security in dynamic offloading for IoT-enabled smart home system.PeerJ Comput Sci. 2024 Aug 23;10:e2211. doi: 10.7717/peerj-cs.2211. eCollection 2024. PeerJ Comput Sci. 2024. PMID: 39314732 Free PMC article.
-
A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications.Sensors (Basel). 2017 Aug 29;17(9):1978. doi: 10.3390/s17091978. Sensors (Basel). 2017. PMID: 28850104 Free PMC article.
-
Fog Computing and Edge Computing Architectures for Processing Data From Diabetes Devices Connected to the Medical Internet of Things.J Diabetes Sci Technol. 2017 Jul;11(4):647-652. doi: 10.1177/1932296817717007. J Diabetes Sci Technol. 2017. PMID: 28745086 Free PMC article. Review.
Cited by
-
Real-Time Compression for Tactile Internet Data Streams.Sensors (Basel). 2021 Mar 9;21(5):1924. doi: 10.3390/s21051924. Sensors (Basel). 2021. PMID: 33803484 Free PMC article.
-
An Overview of Fog Data Analytics for IoT Applications.Sensors (Basel). 2022 Dec 24;23(1):199. doi: 10.3390/s23010199. Sensors (Basel). 2022. PMID: 36616797 Free PMC article. Review.
References
-
- Evans D. The Internet of Things: How the Next Evolution of the Internet Is Changing Everything. [(accessed on 5 September 2020)];CISCO White Pap. 2011 1:1–11. Available online: https://www.cisco.com/c/dam/en_us/about/ac79/docs/innov/IoT_IBSG_0411FIN....
-
- CS Inc. Fog Computing and the Internet of Things: Extend the Cloud to Where the Things Are. [(accessed on 5 September 2020)];CISCO White Pap. 2016 1:1–6. Available online: https://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-ov....
-
- Chang Z., Zhou Z., Ristaniemi T., Niu Z. Energy Efficient Optimization for Computation Offloading in Fog Computing System; Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference; Singapore. 4–8 December 2017; pp. 1–6.
-
- Liu L., Chang Z., Guo X., Mao S., Ristaniemi T. Multiobjective Optimization for Computation Offloading in Fog Computing. IEEE Internet Things J. 2018;5:283–294. doi: 10.1109/JIOT.2017.2780236. - DOI
-
- Hidano S., Murakami T., Katsumata S., Kiyomoto S., Hanaoka G. Model Inversion Attacks for Prediction Systems: Without Knowledge of Non-Sensitive Attributes; Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST); Calgary, AB, Canada. 28–30 August 2017.
LinkOut - more resources
Full Text Sources

